Week 1 Concept Map
Week 2 Concept Map
Week 3 Concept Map
Week 4 Concept Map
Week 5 Concept Map
What are the fundamental concepts that
underlie operating systems?
Our
personal and professional lives are surrounded by a wide range of computer
gadgets in this ever-changing society. Operating systems continue to play an
essential role throughout this rapid transformation. An operating system is
always necessary, whether it be for servers, laptops, or smartphones. Operating
systems evolve and are continuously upgraded as technology progresses. The
principles of Process Management, Memory Management, Disk Storage, I/O
Management, File Directory Structure, Access Matrix, and Protection and
Security have all been introduced and clarified in this course. We have created
a concept map that shows how these elements are connected, thanks to the
guidance provided by the course.
Describe features of contemporary
operating systems and their structures.
Numerous
features found in modern operating systems are intended to maximize computer
system efficiency. Multithreading is one of the most notable of these since it
allows for the simultaneous operation of numerous applications for increased
speed and efficiency. Because virtual memory allocates RAM and hard drive space
dynamically, it is essential to effective memory management. The file directory
structure offers customizable degrees of data management and is available in
multiple formats. Device drivers easily control I/O devices, which include
hardware parts like keyboards, displays, and printers.
Many
operating systems come with strong security and protection built in, providing
defense against a variety of threats from antivirus software to security
features. These dangers include those that are human, physical, and
network-based highlighting the importance of all-encompassing security
measures. The kernel, which manages memory, hardware, and processes, is at the
center of the operating system.
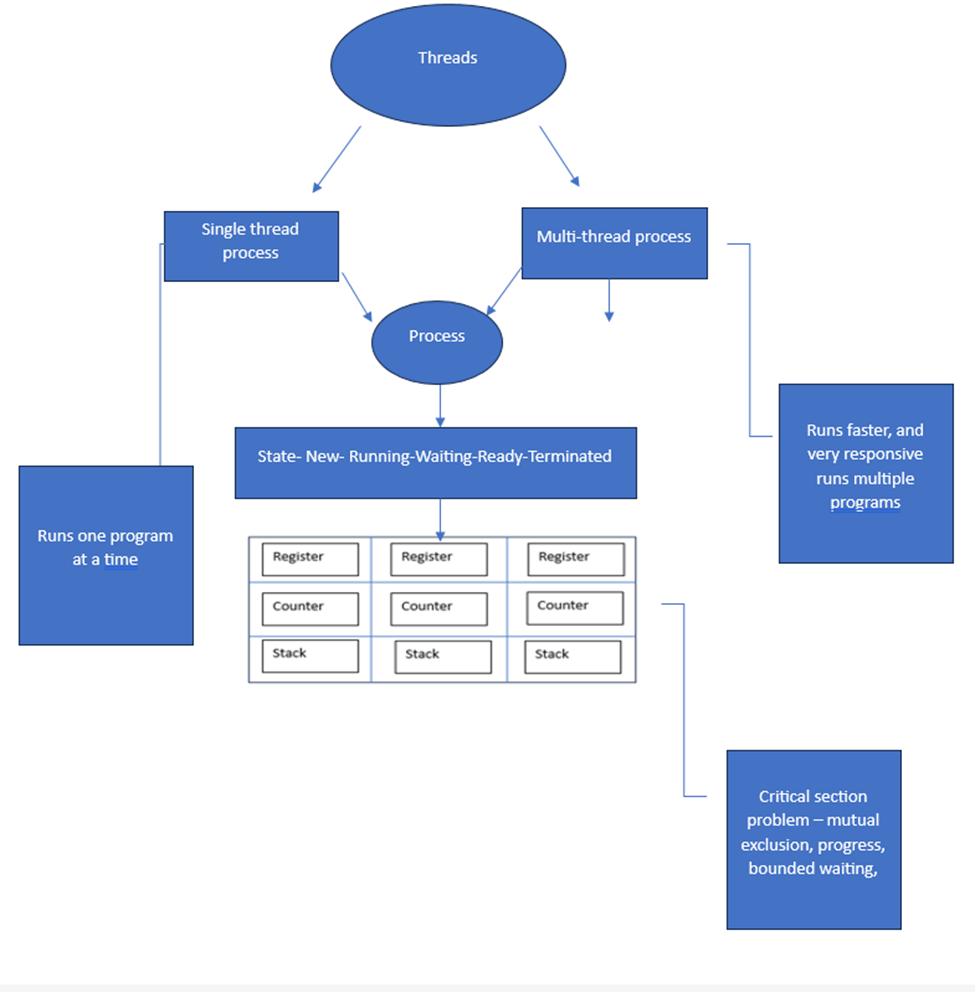
Discuss
how operating systems enable processes to share and exchange information.
An operating system makes use of several related ideas to
enable information sharing and interchange across processes. The process
control block is the heart of this mechanism. It starts in a predetermined
condition and usually moves through the stages of new, running, waiting, ready,
and terminated. Monitoring in the process block includes a register, a record
of open files, a counter that determines the next process, and a count of the
number of active processes. Main memory, resolving key section problems,
virtual memory, the memory management unit, physical address space, and the CPU
are further essential components. Processes cannot share and exchange
information efficiently unless these components smoothly communicate with each other.
Explain
how main memory and virtual memory can solve memory management issues.
Coordinating a computer system's primary and virtual memory can efficiently
address its memory management difficulties. When there isn't enough room to
carry out a procedure, main memory, and virtual memory work together and share
resources to make sure the process runs well. Main memory contains commonly
used data and is renowned for its quick data access. In contrast, virtual
memory allows a process to use more memory than the system can instantly
access, freeing up main memory for other processes. These two memory types work
together seamlessly to create a more efficient operating system.
Explain
how files, mass storage, and I/O are handled in a modern computer system.
Files, mass
storage, and I/O work together in a computer system using a variety of software
and hardware commands to gather data for users. These files can be in Word
documents, music, photos, or any other type of user-generated file. They are
kept on mass storage devices, usually in the form of hard disks stacked like CDs with platter-style architectures. These rotating disks are
read and written quickly by an arm assembly attached to a head. Another
type of storage is the solid-state drive (SSD), which is like a speedier hard
disk but has nonvolatile memory and no moving parts.
Outline
the mechanisms necessary to control the access of programs or users to the
resources defined by a computer system.
Several
mechanisms are used to control access for users or programs, with a particular
emphasis on security and protection. This section controls access to certain
resources inside a computer system, which is also known as authentication.
Authentication verifies the identity of a user or program using key codes,
passwords, or biometric data before granting access. After authorization, several
control mechanisms are activated, such as capability lists and access control
lists. Both lists provide specific access rights, such as read-only,
read-write, delete, execute, or deny, but they manage entire domains that
contain multiple objects.
Recommend
how you will use these concepts about operating systems theory in future
courses and/or future jobs.
The practical
expertise gained from establishing virtual servers and debugging processing
problems is very important when aspiring to become an IT consultant. One of the
most important parts of this experience has been debugging processing problems,
which has helped me find and fix possible mistakes, or performance problems
that can arise in actual situations. I've gained practical problem-solving
skills from this hands-on troubleshooting experience, which will help me assess
complicated problems, identify their underlying causes, and put workable solutions
in place. This knowledge puts me in a good position as an IT consultant, where
the capacity to quickly diagnose and fix technical issues is essential to
provide clients with effectiveness.
References
Barnes,
R. (2020, January 31). Critical Section Problem. Tutorialspoint.com https://www.tutorialspoint.com/critical-section-problem
BYJU’s.
(n.d.). Process in Operating System https://byjus.com/gate/process-in-operating-system-notes/
Meador,
D. (2020, January 31). Single-threaded and Multi-threaded Processes.
Tutorialspoint.com https://www.tutorialspoint.com/single-threaded-and-multi-threaded-processes
Silberschatz,
A., Galvin, P. B., & Gagne, G. (2014). Operating system concepts essentials
(2nd ed.). Retrieved from https://redshelf.com/
Varshachoudhary.
(2023, January 09). Memory Management in Operating System.
https://www.geeksforgeeks.org/memory-management-in-operating-system/